There are a lot of methodologies an organization can use to guide their compliance and security policy and procedures but none of them are silver bullets and none of them understand your unique company operations and culture the way our tailored consulting approach will. We are highly educated and experienced in these methodologies and more. Here are five good methodologies, one process maturity assessment, and one cyber testing tool that can be applied to any recognized methodology:
CYBER SECURITY:
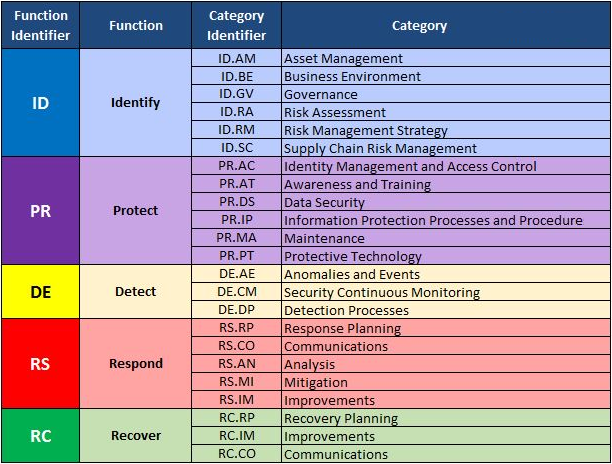
The NIST (National Institute of Standards In Technology) Cyber Security Framework:
- The Framework provides a common language and systematic methodology for managing cybersecurity risk.
- The Core includes activities to be incorporated in a cybersecurity program that can be tailored to meet any organization’s needs.
- The Framework is designed to complement, not replace, an organization’s cybersecurity program and risk management processes.
- The Framework helps guide key decision points about risk management activities through the various levels of an organization from senior executives, to business and process level, and implementation and operations as well.
Fig. 1. Cyber Security Framework Based Policies and Standards, NIST SP 800-53.
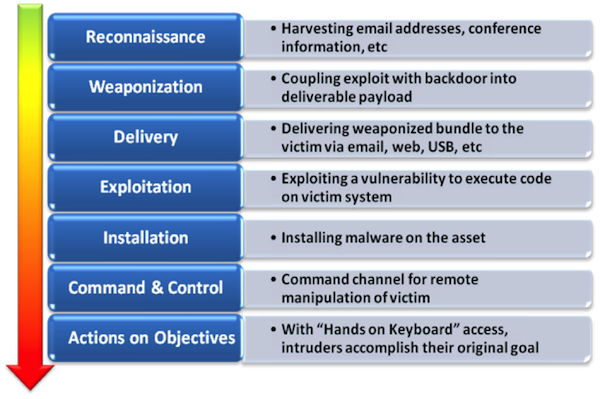
The Lockheed Martin Cyber Kill Chain:
- Developed out of the military and then adapted by Lockheed Martin for the computer network as a lesson learned from the F-22 Fighter jet design intellectual property theft suspected by China.
- It helps you understand the process of cyber and related threat actors at a high level.
- Many data breaches can be traced in part by following this method with other more detailed corroborated information.
- Organizations can conduct red team exercises based on this model to train their security and I.T. staff.
Fig 2. The Lockheed Martin Cyber Kill Chain.
CYBER ASSESSMENT TOOL:
The ICS-CERT’s (Industrial Control System Cyber Emergency Response Team) Cyber security Evaluation Tool (CSET®) is a government-developed guide and tool for cyber security and IT maturity. It covers onsite field assessments, network design architecture reviews, and network traffic analysis and verification. The information gained from CSET® assessments also provides stakeholders with the understanding and context necessary to build effective defense-in-depth processes for enhancing cybersecurity. We at Abstract Forward are trained in running the CSET assessment custom to your company and industry. Contact us here to learn more.
Fig. 3. CSET, Dept of Homeland Security.

PROCESS ASSESSMENT:
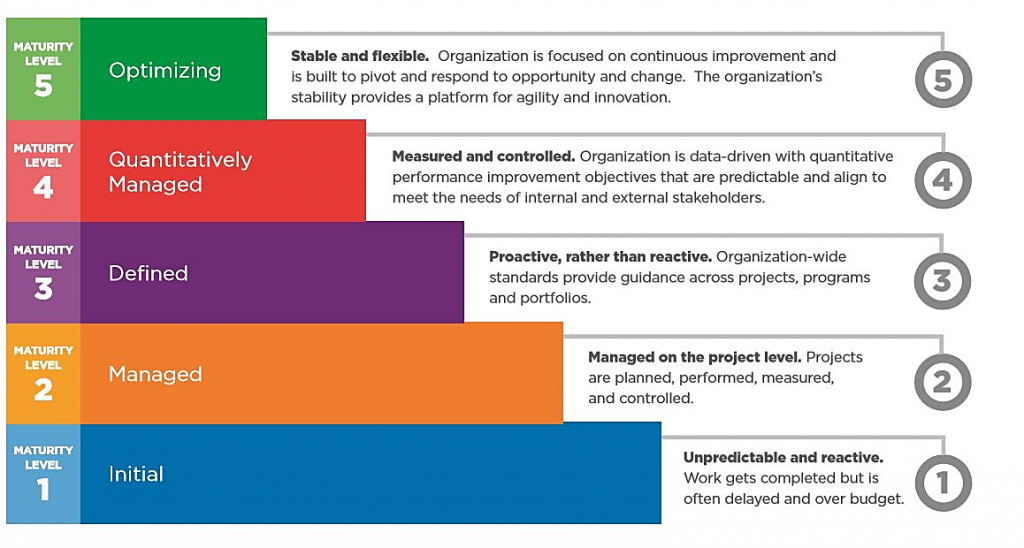
The Capability Maturity Model (CMM)
- Five maturity levels that lay successive foundations for continuous process improvement.
- Each level is characterized by five Key Process Areas (KPA) of product/software development or project management.
- Goals
- Commitment
- Ability
- Measurement
- Verification
Fig 4. The General Capability Maturity Model (CMM).
PROCESS IMPROVEMENT:
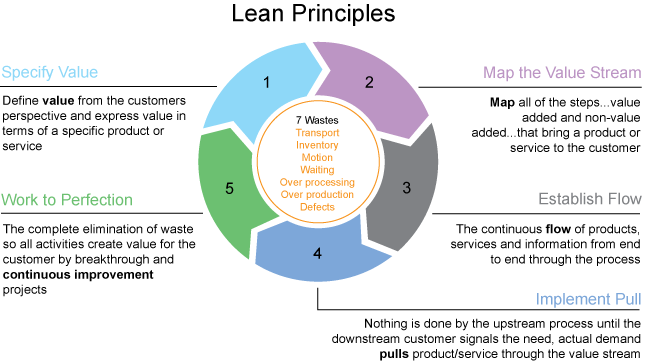
LEAN
- The goal is to provide maximum value to the customer through a perfect value creation process that has zero waste.
- Customer value must – If you don’t meet all three of these criteria, then you have non-value-added activities or waste.
- It must transform the product or service.
- The customer must be willing to “pay” for it.
- It must be done correctly the first time.
- Lean thinking changes the focus of management from optimizing separate technologies, assets, and vertical departments to optimizing the flow of products and services through entire value streams that flow horizontally across technologies, assets, and departments to customers.
- Eliminating waste along entire value streams, instead of at isolated points, creates processes that need less human effort, less space, less capital, and less time to make products and services at far less costs and with much fewer defects, compared with traditional business systems.
Fig. 5. LEAN, IBM.
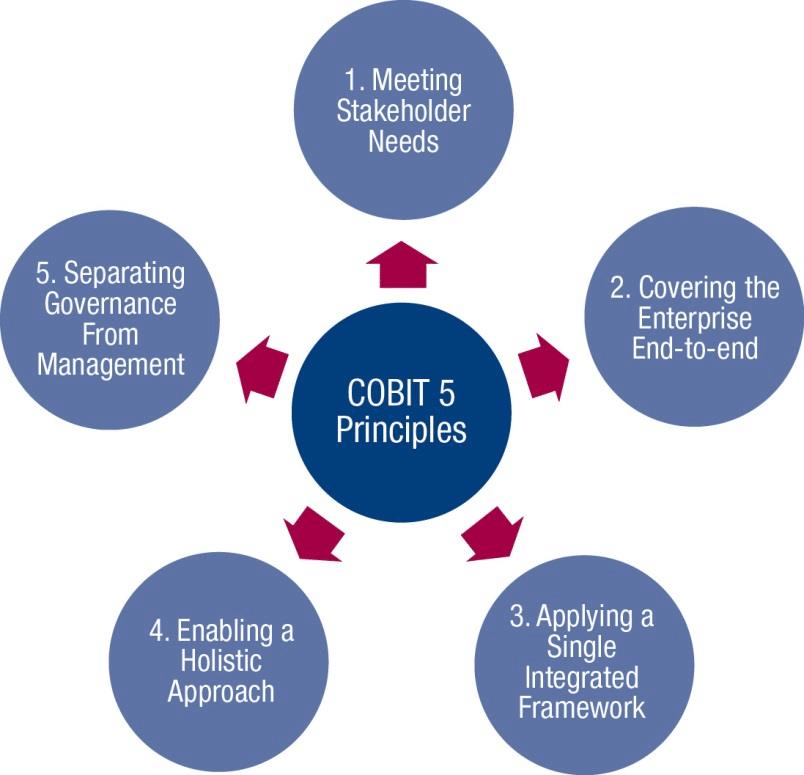
IT QUALITY AND SECURITY:
- Information security principles communicate the rules of the enterprise. These principles need to be:
- Limited in number.
- Expressed in simple language.
- The principles support 3 tasks:
- Support the business.
- Defend the business.
- Promote responsible information security behavior.
- Divides the I.T. related practices and activities of the enterprise into two main areas—governance and management.
Fig. 6. Cobit Principals, ISACA.
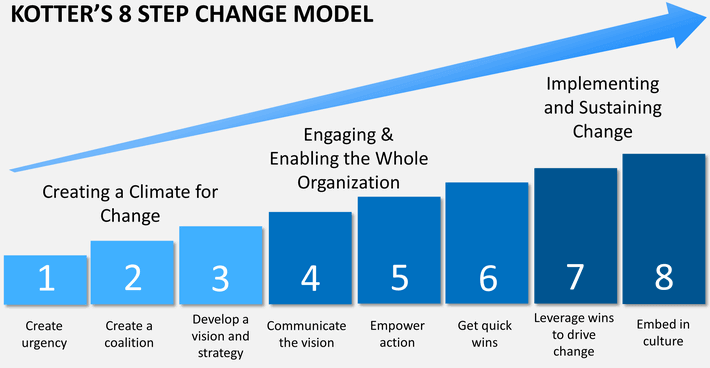
CHANGE MANAGEMENT:
KOTTER’S (HARVARD) 8 STEP CHANGE MANAGEMENT PROCESS:
Respected as one of the most widely used change management guides.
We can customize it for your organization with ease.
- Getting the bosses’ approval and presenting new ideas to disinterested business units rarely secures agreement and inevitably results in resistance.
- For instance, complacency, immobilization, self-protection, deviance, pessimism, and holding back the change.
- Urgency sustains change
Contact us here to learn more.
Fig. 7. 8 Step Change Management Process, Kotter, John P; Harvard).