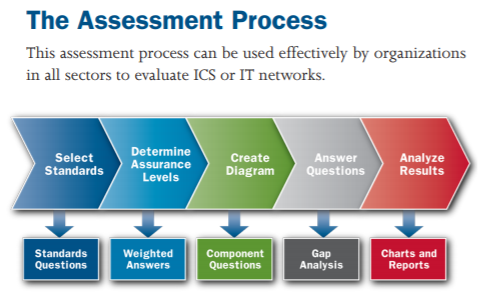
1) Use the Free DHS Developed CSET (Cybersecurity Evaluation Tool) To Assess Your Security Posture: High, Med, or Low.
Figure 1. (DHS, 2018).
2) Educate Employees About Cyber Threats and Hold Them Accountable.
Educate your employees about online threats and how to protect your business’s data, including safe use of social networking sites. Depending on the nature of your business, employees might be introducing competitors to sensitive details about your firm’s internal business. Employees should be informed about how to post online in a way that does not reveal any trade secrets to the public or competing businesses. Use games with training and hold everyone accountable to security policies and procedures.
3) Protect Against Viruses, Spyware, and Other Malicious Code.
Make sure each of your business’s computers are equipped with antivirus software and anti-spyware and updated regularly. Such software is readily available online from a variety of vendors. All software vendors regularly provide patches and updates to their products to correct security problems and improve functionality. Configure all software to install updates automatically. Especially watch freeware which contains malvertising.
4) Secure Your Networks.
Safeguard your Internet connection by using a firewall and encrypting information. If you have a Wi-Fi network, make sure it is secure and hidden. To hide your Wi-Fi network, set up your wireless access point or router so it does not broadcast the network name, known as the Service Set Identifier (SSID). Have a secure strong password such as (xeyg1845%RELIGO) to protect access to the router.
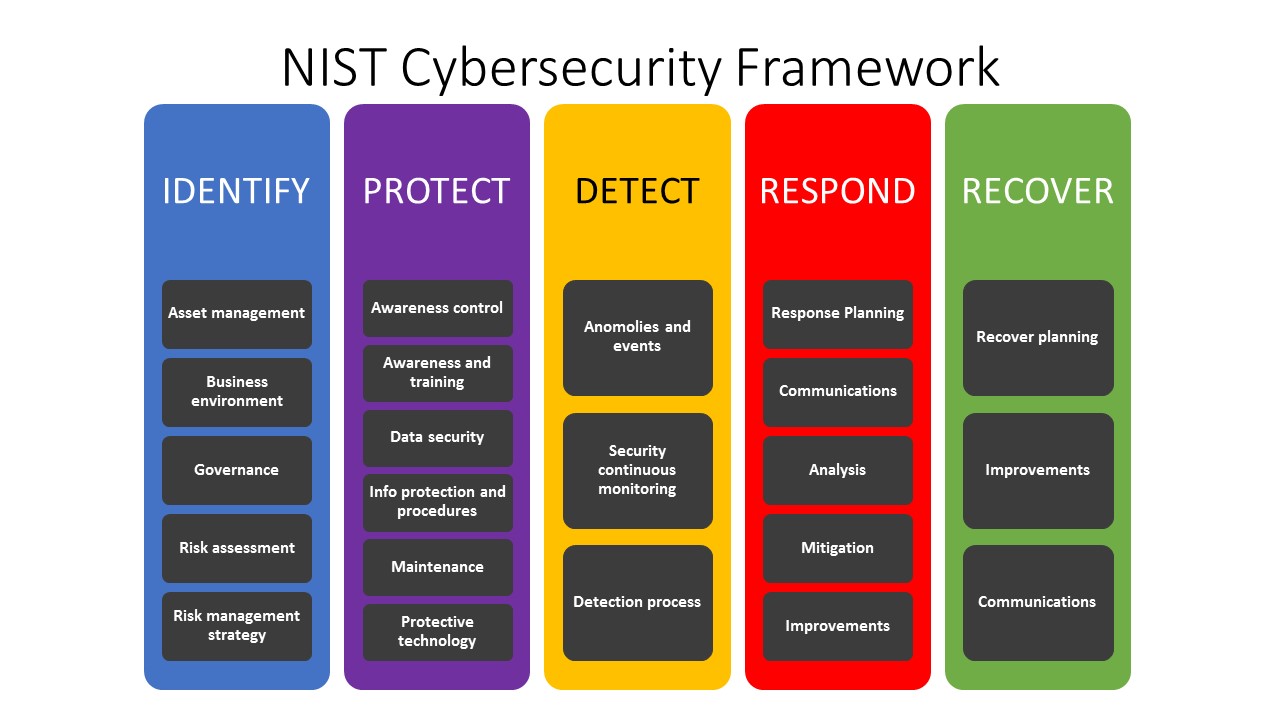
5) Base Your Security Strategy Significantly on the NIST Cybersecurity Framework 1.1: Identity, Detect Defend, Respond, and Recover.
Fig. 2. (NIST, 2018).
 6) Establish Security Practices and Policies to Protect Sensitive Information.
6) Establish Security Practices and Policies to Protect Sensitive Information.
Establish policies on how employees should handle and protect personally identifiable information and other sensitive data. Clearly outline the consequences of violating your business’s cybersecurity policies and who is accountable.
7) Require Employees to Use Strong Passwords and to Change Them Often.
Consider implementing multi-factor authentication that requires additional information beyond a password to gain entry. Check with your vendors that handle sensitive data, especially financial institutions, to see if they offer multi-factor authentication for your account. Smart card plus pass-code for example.
8) Employ Best Practices on Payment Cards.
Work with your banks or card processors to ensure the most trusted and validated tools and anti-fraud services are being used. You may also have additional security obligations related to agreements with your bank or processor. Isolate payment systems from other, less secure programs and do not use the same computer to process payments and surf the Internet.
9) Make Backup Copies of Important Business Data and Use Encryption When Possible.
Regularly backup the data on all computers. Critical data includes word processing documents, electronic spreadsheets, databases, financial files, human resources files, and accounts receivable/payable files. Backup data automatically if possible, or at least weekly, and store the copies either offsite or on the cloud.
10) Control Physical Access to Computers and Network Components.
Prevent access or use of business computers by unauthorized individuals. Laptops can be particularly easy targets for theft or can be lost, so lock them up when unattended. Make sure a separate user account is created for each employee and require strong passwords. Administrative privileges should only be given to trusted IT staff and key personnel.
11) Create A Mobile Device Protection Plan.
Require users to password protect their devices, encrypt their data, and install security apps to prevent criminals from stealing information while the phone is on public networks. Use a containerization application to separate personal data from company data. Be sure to set reporting procedures for lost or stolen equipment.
12) Protect All Pages on Your Public-Facing Web-pages, Not Just the Checkout and Sign-Up Pages.
Make sure submission forms can block spam and can block code execution (cross side scripting attacks).
Contact Abstract Forward here for more info.
