The coronavirus disease (COVID-19) is being used in a variety of malicious/hacking campaigns including email spam, ransomware, BEC (business e-mail compromise), malware, drive-by downloads, and even fraudulent domains. The mention of current events in malicious cyber-attacks is nothing new as threat actors often use current events and popular personalities in their social engineering strategies.

As the number of those infected continues to increase, campaigns that use the disease as a lure are likely to also increase because people tend to get excited about trending information and they click without double-checking, especially when their defenses are down in this emotional and media-hyped context. Let facts and science rule the day, not speculation and sensationalized news media. As we seek recovery and healing, the last thing we need is the double whammy of being hacked, scammed, or the victim of ransomware. Don’t let that be you, always double-check.
Here are some detailed internet hygiene and scam avoidance tips (compiled from the FTC, Trend Micro, and Symantec):
- Don’t click on links from sources you don’t know. They could download viruses onto your computer or device.
- Trend Micro identified the following exploits as of 03/16/20 and more are likely coming. Five of which were .exe or executable files – very high risk.
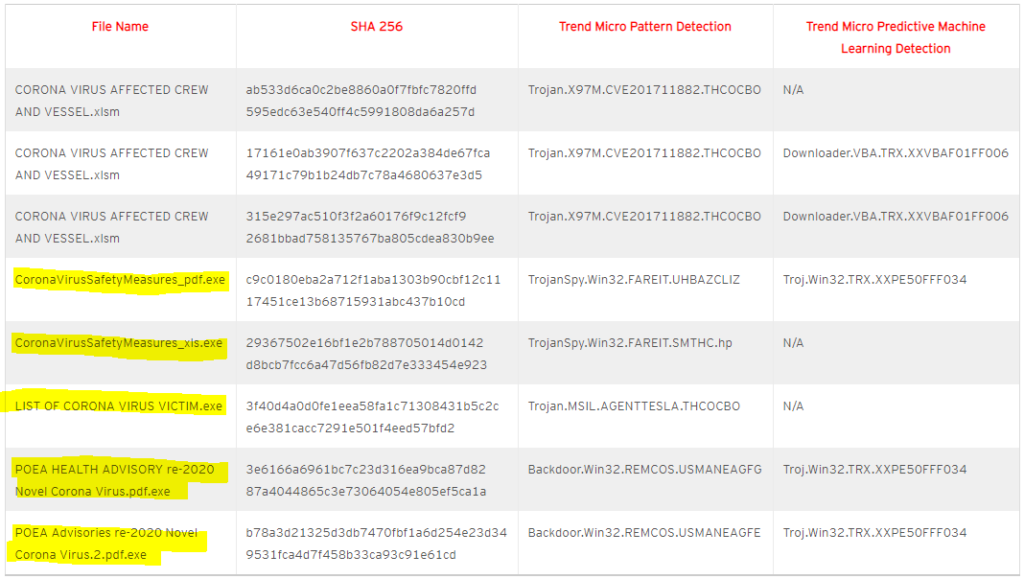
- Watch for emails claiming to be from the Centers for Disease Control and Prevention (CDC) or experts saying that they have information about the virus.
- For the most up-to-date information about the Coronavirus, visit the Centers for Disease Control and Prevention (CDC) and the World Health Organization (WHO).
- Symantec Identified the following Fake example:
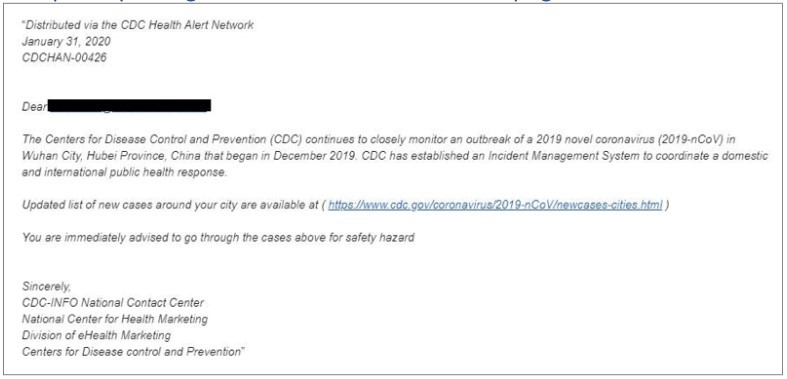
- Ignore online offers for vaccinations. There currently are no vaccines, pills, potions, lotions, lozenges or other prescription or over-the-counter products available to treat or cure Coronavirus disease (COVID-19) — online or in stores.
- Report any suspected product scams to the FTC here – scroll to the bottom for reporting link.
- Do your homework when it comes to donations, whether through charities or crowdfunding sites. Don’t let anyone rush you into making a donation. If someone wants donations in cash, by gift card, or by wiring money, don’t do it.
- Beware of online requests for personal information. A coronavirus-themed email that seeks personal information like your Social Security number or login information is a phishing scam. Legitimate government agencies won’t ask for that information.
- Never respond to email by giving your personal data.
- Check the email address or link. You can inspect a link by hovering your mouse button over the URL to see where it leads. But keep in mind phishers can create links that closely resemble legitimate addresses. Never go to HTTP only sites but look for the HTTPS. Use the trend micro URL checker here but know it won’t catch all bad sites but is a good start.
- Watch for spelling and grammatical mistakes. If an email includes spelling, punctuation, and grammar errors, it’s likely a sign you’ve received a phishing email.
- Look for generic greetings. Phishing emails are unlikely to use your name. Greetings like “Dear sir or madam” signal an email is not legitimate.
- When in doubt, don’t open, block, and delete.
Lastly, with so many people working from home amid the pandemic, our next podcast will deal with IAM / vendor risk mgmt., and the related work from home network security considerations — coming around April/May 2020! Follow our podcast here.
Wishing you, your family, and the greater community — strength, healing, innovation, and fast recovery. Together we can get through this.
